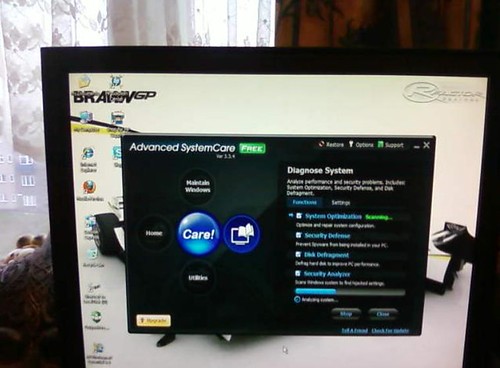
As we live in this modern world so we can use different endpoint techniques by having different ways. The term endpoint security is not much common for today’s modern man as he don’t know about the basic concept of this term. The basic concept of this term is that the whole system (included its entire parts) is liable for the protection of computer system against any destructive virus. The most commonly used way of fixing any security risk is through endpoint security.
To understand the system or program it is necessary to look into the working of that system. Endpoint security is responsible for the protection of the system from malwares. There are some security software like firewalls and the antivirus that gives the way out of protection from the viruses. The Endpoint security is installed in the system and it will provide you all kind of guidance to use it and helps you to solve the security problem.
The user of the client computer is now free from owning the security software individually, as server is now liable to secure the clients with having only one security endpoint in it, that ultimately shows a saving of clients in regard of money and time. The server computer makes the clients secure from all kinds of security problems when it gets connected to the internet.
The most commonly used endpoint security is the firewall and the antivirus. Besides these two now there are also some other protections are available in the market and you can also get them from internet to make your system as protected as you want it to be.
In this ever growing world a huge variety of security systems are available for the personal computers as well as for those companies who are working on massive computer networks. In huge computer arrangements the server can easily control and maintain the security lapses that might comes in its any endpoint at any stage.
Our computer system can be affected by viruses through both internal and external devices (flash drive, data cables etc) that we use in excess with our computers as a routine thing. As the external devices are the surest way of entering virus in our computer so endpoint security allows us to secure our system from all kinds of viruses that might damage our computer system due to the usage of external devices. In the same way endpoint security system also make it possible for us to secure our systems from those viruses that might attack on our computer system due to the usage of internet. Apart from all these facilities endpoint security system allows the server to control and observe all the activities of its endpoints for security purposes so the server can lock the external devices as well as it can prohibit the installations of any kind of software from internet on its endpoints due to security reasons.
If you have started a business with large number of people and computers and you don’t want your employees to misuse the computers in any way and if you also don’t want to give the complete authority of using computers to your employees with a threat that they might misuse it, that may cause any security problems, then you need not to worry any more because you can monitor and control all the activities of your all employees right from your computer by using endpoint security system. By using endpoint security you can expand the security of your network as much as you can.
lunes, 4 de abril de 2011
viernes, 1 de abril de 2011
Work force of the modern era is dynamic. Employees are interested in balancing their personal as well as the professional lives. The fierce competition has made it difficult to get new business clients from the traditional business environment. In such circumstances, the benefits provided by the remote desktop solutions are worth for the employees as well as for the employers.
Remote desktop has made it easy for the employees to do their official work even not staying in office for a long period of time, it means that they can access their personal computers even far from their office setting. This latest technology has allowed the employees to work on their personal computers at any time and at the same time they can store a huge amount of information on it for further perusal of their work. The usage of remote desktop has become so frequent now a day that most of the employees can’t even think to work without it, as they start taking it as a basic source of their effective work and large output. This facility enables the employees to get their required data at any time and from anywhere, either they are available at the work location or anywhere else.
The preference of the employees to work away from the workplaces is because of many reasons. The foremost reason could be some important home task. Employees can switch from the offices if some important task is waiting for them at home, to manage both sides efficiently. The new remote desktop provides the best solution for the employees who want to work with fulfillment of house duties also. Because of remote desktop neither company’s profits got cut down nor personal life of employees is compromised because it helps them perform efficiently on all grounds.
Apart from previously mentioned advantages there are certain more advantages that makes it a most useful technique rather than the traditional business strategies and that benefit is its capacity of saving time. It majorly shortens down the specific time that always occurs during sales process. The sales process usually proceeds from the salesperson to the customer in a way that the salesman provides a contract to the customer and customer takes that contract with him for some time for his through study and understanding, after completely understanding the contract the customer usually signed it, and all that process takes a long period of time. The time period can be from few hours to few weeks and it always depends upon the salesman’s credibility among the customers. In this modern competitive world wastage of even a single minute can lead the business towards huge loss. So to remain competitive in this ever growing world it is necessary to decrease the suitcase time till zero by getting all the required data in the blink of eye, and the remote desktop is providing this opportunity to its users in a better way.
Besides many advantages, risk regarding theft of official information is also associated with the data access systems. Remote solutions use VPN connections that provides fully secure services, hence no fear of data outflow. The most secure connections are VPN connection that provides the secure access to an employee’s computer without information loss.
Another advantage of remote desktop is that employees can work according to their feasibility and their own style at any time. When the employees get the full independence on their work then it will automatically raise their satisfaction level and that will alternately buildup their confidence regarding their work. Remote desktop has given the relaxation to the employees that they can easily fix their work time by looking at their personal duties. So by using remote desktop employees can work whenever they feel free and relax right from their homes. This strategy is not only beneficial for the employees but it is equally profitable for the company too.
As the employees work for the company from their houses, so their absence can’t be felt by the company. By using remote desktop most of the operating expenses can also be ruled out, as the employee can’t used the office inventory by working from his home so this helps the company in reducing its expenses. The ever changing business world requires the employee’s mobility for the purpose that anything can be delivered to the exact location without any delay. As the working environment is changing day by day so the demands of employees are also changing and the best way to get the business in the market is to satisfy the employees in the best way by providing them the favorable working environment. The best way to meet the employee’s demands is to apply remote desktop strategy in the business.
Remote desktop has made it easy for the employees to do their official work even not staying in office for a long period of time, it means that they can access their personal computers even far from their office setting. This latest technology has allowed the employees to work on their personal computers at any time and at the same time they can store a huge amount of information on it for further perusal of their work. The usage of remote desktop has become so frequent now a day that most of the employees can’t even think to work without it, as they start taking it as a basic source of their effective work and large output. This facility enables the employees to get their required data at any time and from anywhere, either they are available at the work location or anywhere else.
The preference of the employees to work away from the workplaces is because of many reasons. The foremost reason could be some important home task. Employees can switch from the offices if some important task is waiting for them at home, to manage both sides efficiently. The new remote desktop provides the best solution for the employees who want to work with fulfillment of house duties also. Because of remote desktop neither company’s profits got cut down nor personal life of employees is compromised because it helps them perform efficiently on all grounds.
Apart from previously mentioned advantages there are certain more advantages that makes it a most useful technique rather than the traditional business strategies and that benefit is its capacity of saving time. It majorly shortens down the specific time that always occurs during sales process. The sales process usually proceeds from the salesperson to the customer in a way that the salesman provides a contract to the customer and customer takes that contract with him for some time for his through study and understanding, after completely understanding the contract the customer usually signed it, and all that process takes a long period of time. The time period can be from few hours to few weeks and it always depends upon the salesman’s credibility among the customers. In this modern competitive world wastage of even a single minute can lead the business towards huge loss. So to remain competitive in this ever growing world it is necessary to decrease the suitcase time till zero by getting all the required data in the blink of eye, and the remote desktop is providing this opportunity to its users in a better way.
Besides many advantages, risk regarding theft of official information is also associated with the data access systems. Remote solutions use VPN connections that provides fully secure services, hence no fear of data outflow. The most secure connections are VPN connection that provides the secure access to an employee’s computer without information loss.
Another advantage of remote desktop is that employees can work according to their feasibility and their own style at any time. When the employees get the full independence on their work then it will automatically raise their satisfaction level and that will alternately buildup their confidence regarding their work. Remote desktop has given the relaxation to the employees that they can easily fix their work time by looking at their personal duties. So by using remote desktop employees can work whenever they feel free and relax right from their homes. This strategy is not only beneficial for the employees but it is equally profitable for the company too.
As the employees work for the company from their houses, so their absence can’t be felt by the company. By using remote desktop most of the operating expenses can also be ruled out, as the employee can’t used the office inventory by working from his home so this helps the company in reducing its expenses. The ever changing business world requires the employee’s mobility for the purpose that anything can be delivered to the exact location without any delay. As the working environment is changing day by day so the demands of employees are also changing and the best way to get the business in the market is to satisfy the employees in the best way by providing them the favorable working environment. The best way to meet the employee’s demands is to apply remote desktop strategy in the business.
lunes, 28 de marzo de 2011
Remote Management Service Hard Drive
Managed IT Services are becoming a beautiful proposition for businesses hoping to reduce costs while increasing productivity.
Business
Today�s customers expect in excess of quick difficulty shooting of devices and systems.� They anticipate assured system availability and all-inclusive help for the put in products. Distant services play a crucial function in fulfilling the client expectations. Distant services take on consistent monitoring of system situations and real-time remote admission to buyer systems.
Right from the second you commence to adopt our options in your business, you're bound to witness a never-before expertise relating to enhanced valuation and the reliability of your company operations!
The rules of engagement -
A acceptable vender would be able to take care of all client necessities while ensuring that every guidelines of operations laid down by governing bodies and the nearby government are followed. It is preferred to go together with a seller who is licensed by international institutions for method and quality. Limitations such as data security, reporting, use of licensed computer software are fundamental when outsourcing operations toward a vendor. Quite a few smaller sellers would are likely to use unaccepted practices in order to cut costs. A thorough audit of the operations
The remote control service platform can be provided in 3 varied online connectivity modes, constant mode, Ad-hoc mode and disconnected mode. Security is provided with main significance in remote service platform as the prosperity of the remote control services heavily will depend on buyer adoption.
Data encryption in the course of transmitting and computer storage ensures privateness for sensitive data. You can find no have need of for secure lockup of physical tapes. Just as charge efficiencies can be disseminated via specialised IT firms, so can certainly the latest security procedures. Distant backup service corporations take security methods as section of their primary business, meaning their customers do not have to attempt to achieve this as well.
Binary Information Compression
Transferring only the binary information that has evolved from one day to the next, is another technique to added reduce net work traffic. It is just like the open source file shift service referred to as Rsync. As an alternative to move complete files, higher via the internet backup service providers prefer to utilize this method.
Lots more revealed about remote management service here.
Dodie Zeitlin is our current Remote Management Service spokesperson who also reveals secrets software list,exchange 2000 anti virus,microsoft software downloads on their web resource.
viernes, 25 de marzo de 2011
Remote Backup Automation Billing System
I dialogue a large amount about remote control information backup software programs and backup programs in general.�� My drive got filled with malware whilst I used to be downloading several internet documents for my research examine just days ago.� Since I have been reading about malware concerns and it really is result on computer systems, I right away identified that I used to be indeed infected.� Owing to I exploit a backup package with all my computer systems I was able to restore the whole lot back to normal, in record time and easily.
Remote Backup
What about the "Digital Divide", "Digital Age Dilemma" - wherever too many voters are at a loss of access to the globe of digitization? Did a robot take your job? Did a pC software make you obsolete? Information Mining, is it alive and well? Is it/was it a desire to get up and go to work and be given a pink, blue, brown, or/and purple colored separation notice that was dated yesterday and efficient now?
Evaluate the business:
It's at all times a great plan to ascertain any contractor that you intend to carry out enterprise with. The difficulty is, how do you consider these sorts of companies until they offer you a method on their website, (that will likely turn into biased).
Observing the institution; the researchers determined to suggest a computerized patient monitoring and billing system that is meant to unravel the concerns that they discovered. Useful patient monitoring and billing management significantly impact areas of a Local Group Hospitals such as medical-related services, billing policies and cost rates. Using the help of this proposed computerized system the City Community Hospitals can simply keep monitor and maintain each patient's information.
The backup will then mirror the state of your system when you install the program. This way, you can rest assured that vital files will not become missed. On the same note, your computer software tend to be kept up to date immediately each few days which means that necessary records that have been added later will not be missed.
Finally, it is quite apparent that redundancy occurs to rank among one of many most important elements for whichever kind of service providers was considered to back information up online. This can be as it is important to have more than one copy of every file. These multiple copies need to be kept at all levels of creating the data needs of the company under question.
Data Flexibility
Mission crucial data, even if it really is 10 days or ten yrs. old, demands a elevated stage of accessibility in order to offer the necessary versatility to meet business opportunities. Distant backup services are accessed via only one factor via a nET connection. Instead of needing to hunt down tapes, the data is prepared for any end user to swiftly retrieve. Possessing data obtainable at one's fingertips permits every staff member to really concentrate their interest on their objectives in place of technological know-how or having to call for IT support.
Lots more revealed about remote backup automation here.
Ambrose Bartoldus is todays Remote Backup Automation specialist who also discloses information software list,usb missile launcher with webcam,improve concentration on their blog.
viernes, 18 de marzo de 2011
Control Pc Remote Control Pc Remote
However it is a common situation that every plans to have a splendid rest flop similar to that of a bubble. Probably the most annoying is that vocations are commonly spoiled because of matters far much less notable than a flood. Merely the manager has forgotten in what folder is the required file, or a close pal needs many PC-related help. Also there are actually such CEOs that don't care about staff members being on the other end of the world, and need to see them the subsequent day in the office just to maintain a fifteen minute meeting.
Control Pc Remote
Still all upper outlined instances have the very first thing in common. They can be easily solved using the PC handheld remote control program. And Anyplace Handle Software is glad to introduce such a program that is not solely on guard of the peaceable holidays however keeps fuss away all of the yr round.
Anyplace Handle is PC remote control programme capable of displaying remote PC desktop and allows employing only community keyboard and mouse to regulate it remotely. And the ingenious online connectivity scheme maintains remote device accessible from anywhere in the world that's connected to the web. While some other piece of good news is that Anyplace Control is router- and firewall-friendly, so there exists no need to become a system administrator to hook up the required computers. And on best of the cream is the improved video panel grabbing element that provides the important consolation in the course of PC handheld remote control session, so it's not that difficult to fail to remember that your currently engaged on a PC situated 100 miles away.
Besides its main PC handheld remote control aspect Anyplace Control allows direct file exchange using the target device as well. All sorts of personalized data, presentations, lethal crucial reports, and even million dollar value contract can be transferred directly with Anyplace Control file transfer attribute protected with CHAP authentication and RC4 128-bit random key. And this signifies that spam arrester blocking e-mail attachments or FTP being down won't make the work to halt again.
You in no way know whenever when possessing PC remote control computer software is going to be the solution that you desperately have need of in an emergency.
Find out the secrets of control pc remote here.
Walker Gebhart is our current Control Pc Remote specialist who also informs about spyware doctor with antivirus,research paper writing software,fun usb gadgets on their web site.
jueves, 17 de marzo de 2011
Control Desktop Pc Remote Access Remote Ac
Not to be baffled while using the handheld remote control we use on our televisions, handheld remote control software, also referred to as Remote Desktop Program or remote control access software, allows for a worktop computer or world wide web enabled system to be accessed and managed by a second laptop or net enabled device. This means that an iPhone utilizer might with ease log onto a (consenting) friend's computer, take full handle of their machine, and use it to entry the web, play a game, or do any of a host of different things.
The great thing about these items is that distance makes no variation to the standard of the connection. A consumer in Ireland may as with ease take handle of a computer within the United States as they would just one in the very next room. Some individuals make use of this software programs to look in on the security of their home or the security of their animals whilst at work or on vacation.
Let's say a close mate of yours is a few yrs. behind the times. They have ultimately determined to purchase their initial computer, but have little or no working knowledge of them. This is now where Remote Handle Software comes in. Once you acquire past the first of guiding their situation by way of the installation and setup of the software, it comes to be a very easy process - just connect... and you are done!
Many people who are enthusiastic about informatics have got to respond to the adjurations of a parent or of a buddy who asks for assistance, assist or beg for a miracle to resolve any bagatelle on their very own PC. One time offers you happiness to determine that your helping, the next kind of the same, however at the third request of assistance you begin placing into balance the some time and general the kilometers, whenever the PC is way away.
But here: the IT discipline proposes itself as a legitimate device of intervention on a PC that isn't your own, letting integral the inviolable and untouchable right of proprietorship of the congenial informatics geeks of not ping removed from their position. These are: remote desktop management and remote control aid for Mac.
machine, and apply it to access the web, play a game, or do any of a host of
other things. The beauty of these goods is that distance makes no difference
to the quality of the connection. A consumer in Eire may just as simply take
control of a pC in the United States as they might one in the very next
Find out the secrets of control desktop here.
Harold Hotek is our current Control Desktop commentator who also informs about monitor civil war,fun usb gadgets,compare newegg on their site.
Pc Remote Access Remote Ac
The great thing about these items is that distance makes no variation to the standard of the connection. A consumer in Ireland may as with ease take handle of a computer within the United States as they would just one in the very next room. Some individuals make use of this software programs to look in on the security of their home or the security of their animals whilst at work or on vacation.
Let's say a close mate of yours is a few yrs. behind the times. They have ultimately determined to purchase their initial computer, but have little or no working knowledge of them. This is now where Remote Handle Software comes in. Once you acquire past the first of guiding their situation by way of the installation and setup of the software, it comes to be a very easy process - just connect... and you are done!
Many people who are enthusiastic about informatics have got to respond to the adjurations of a parent or of a buddy who asks for assistance, assist or beg for a miracle to resolve any bagatelle on their very own PC. One time offers you happiness to determine that your helping, the next kind of the same, however at the third request of assistance you begin placing into balance the some time and general the kilometers, whenever the PC is way away.
But here: the IT discipline proposes itself as a legitimate device of intervention on a PC that isn't your own, letting integral the inviolable and untouchable right of proprietorship of the congenial informatics geeks of not ping removed from their position. These are: remote desktop management and remote control aid for Mac.
machine, and apply it to access the web, play a game, or do any of a host of
other things. The beauty of these goods is that distance makes no difference
to the quality of the connection. A consumer in Eire may just as simply take
control of a pC in the United States as they might one in the very next
Find out the secrets of control desktop here.
Harold Hotek is our current Control Desktop commentator who also informs about monitor civil war,fun usb gadgets,compare newegg on their site.
miércoles, 16 de marzo de 2011
Configuration Management Pmp Exam Prep
Configuration Management and its Quite a few Uses
Managing Configurat
The Definition of Configuration Management
The formal definition of configuration management is as follows:
Configuration Administration - a method to make sure that the inter-relationships of various versions of infrastructure hardware and software are documented precisely and efficiently.
Network Configuration Collection
Provide automated and manual alternative for acquiring configuration from any community device. Equipment that supplied by gear sellers aren't good enough as a result most networks using a variety sellers and types of community gadgets similar to switches, routers, firewalls and different network devices. Applying generic SNMPv1/2 or secured SNMPv3 protocols can easily furnish central community configuration management system for the entire organization.
Network Configuration Backup
Create duplicate configuration of all network systems including all of the configurable prices that have been discovered for each network device. The backup system maybe automated for particular dates and times or produced by user request. The backup should include incremental and differential configuration settings for each community device.
For all of your requirements of 24x7 Server configuration management, hosting service support, server security, remote control hosting service management, for Windows and Linux servers - contact us now - http://
The invention of the SCCB, SCM group, and all of the processes, procedures, plans and requirements called for here will likely to be in addition to work needed to determine a resource library device and a librarian that are minimal needs for the average software programs project. These groups and documentation will take considerable work to implement and ought to be defined as an area of the project scope if they're to be undertaken.
Another necessary guideline is to develop a clear baseline plan (i.e.: the task description as described at the beginning of the project), diverse variations all through development, in addition to the ultimate venture as released. This can be in contrast to the lean development techniques, which tend not to outline a clear baseline plan or use formal task configuration management.
Lots more revealed about configuration management here.
Douglas Fiorella is your Configuration Management specialist who also reveals secrets cell phone wallpapers,acer laptop ebay,acer laptop ebay on their own site.
Suscribirse a:
Entradas (Atom)